Fight the phish!
It can be easy to fall for phishing schemes and other scams hook, line, and sinker. With a little education and precaution, however, all of us can more confidently identify, report, and delete suspicious emails when we receive them.
Below, you'll find information on how to spot some common red flags in phishing schemes and how to report suspicious emails. You can also review some of the most common scams sent to University of Utah community members.
If you receive a suspicious email similar to the examples on this page, don’t hesitate to report it using the Phish Alert Button in your email client or by forwarding it as an attachment to phish@utah.edu.
“Phishing” is an IT term for a cybercrime in which people try to fool other people into sending them money or revealing personal information online. The name comes from the idea of fishing: Scammers send a message that acts as bait, hoping to “hook” someone.
The good news is that you have the power to throw these phish back! Let’s take a minute to talk about what you can do to avoid phishing.
First, be cautious. Remember the old warning about not talking to strangers? It goes double on the internet, since anyone can pretend to be anyone else and an email from an exciting new friend could actually be a trick.
Second, remember not to share sensitive information through emails. No legitimate organization would ask for personal details, such as your passwords, credit card numbers, and Social Security Number in an email.
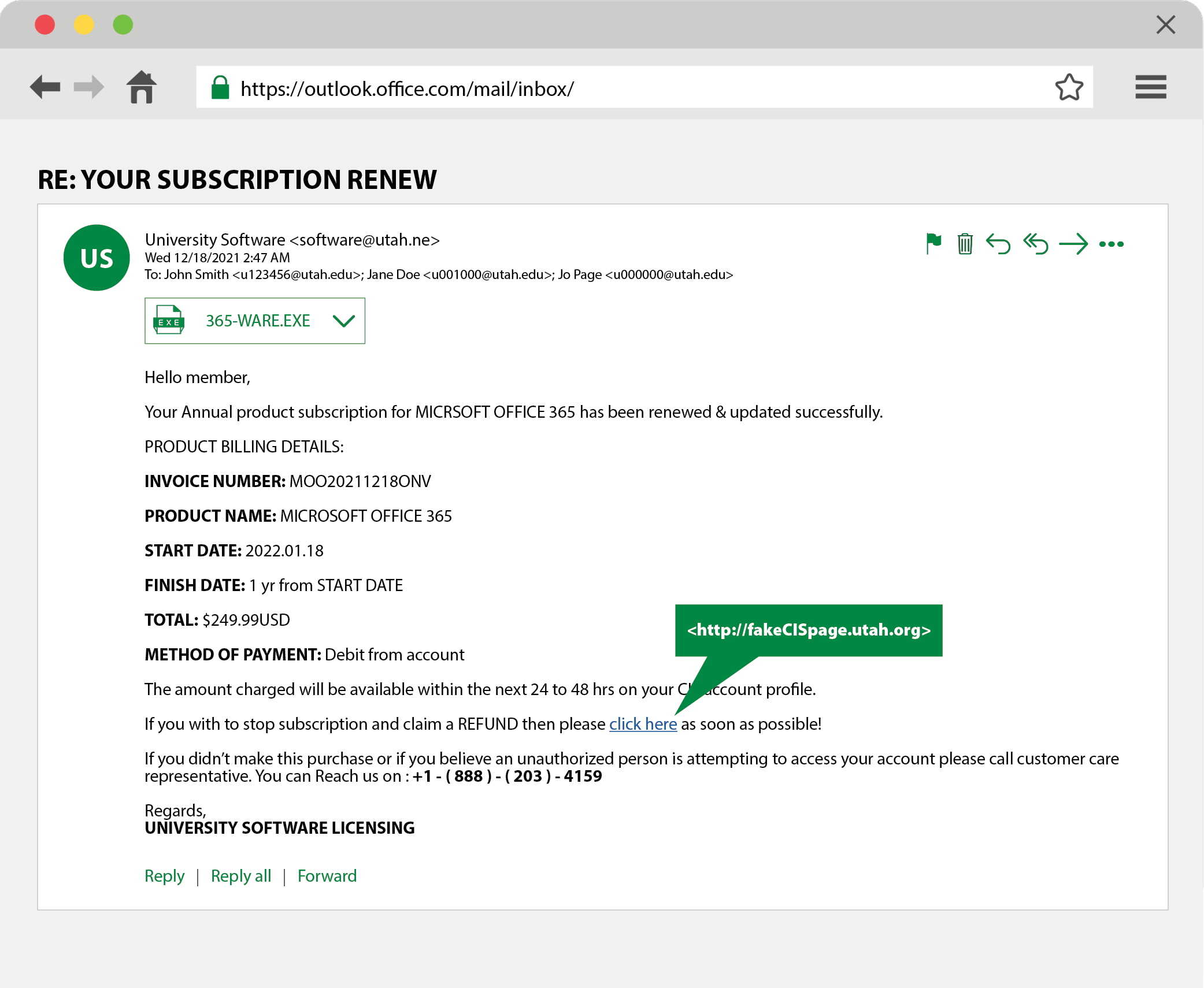
Anatomy of a phish: Common red flags
Some key indicators of a phishing scheme or scam include:
Time stamp
- It's outside of work hours or late at night
Other recipients
- You are among a group of people you don't know
Sender
- The sender isn't someone you know
- The sender is outside of your organization
- The sender's email address impersonates someone you know
- The email address contains a suspicious domain or spelling errors
Greeting
- It's generic, unusual, or missing
Subject
- It's a reply to an email you did not send
- It does not match the message's content
- It contains spelling, punctuation, or grammar errors
The message
- It's unexpected
- It creates a sense of urgency (e.g., "Respond ASAP!")
- It asks you to do something in order to avoid a negative consequence or to gain something of value
- It requests personal information
- It asks you to update or verify an account
- It contains repeated spelling, punctuation, or grammar errors
- It gives you an uncomfortable gut feeling
The email above is a phishing scheme. Can you spot all the red flags? Select the image to view a larger version.
Attachment(s)
- You weren't expecting an attachment
- It's a potentially dangerous file type
Hyperlink(s)
- It includes misspellings
- It's displayed with no additional information
- It's been shortened
- It indicates a different website when you hover over the text
Signature
- It's generic, unusual, or missing
Below are some common tactics that criminals use when phishing University of Utah students, faculty, and staff, and University of Utah Health personnel. These examples are intended to help every U of U user learn how to spot a phish. Use the links to access an overview and example of each tactic (login required). For a list of recent phishing attempts, please visit the Phishing page (login required).
Job offers
If you receive a job offer that seems too good to be true, it may be an employment scam. Scammers often target students, offering large amounts of money for little work.
Impersonation
Criminals often use email addresses that impersonate the university, maybe even students, colleagues, or professors, and reputable companies. Impersonators might request gift cards, phone numbers, or additional personal information, or offer opportunities to good to be true.
Calls to action
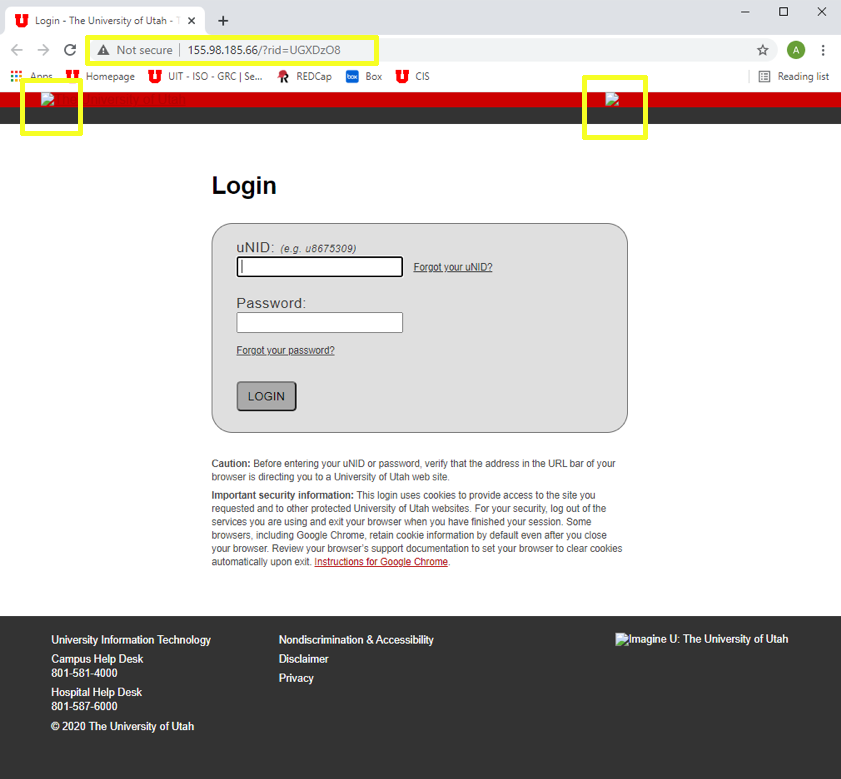
Criminals often try to gain access to your university credentials by sending emails that indicate an issue with your password, email, or other online accounts. They may also ask you to log in to make updates. The emails usually include an urgent call to action and contain links to a malicious webpage.
Suspicious links
If you receive a suspicious email with a link, don’t click! Instead hover your mouse over the link text to reveal the real address and see if the URL matches what's in the email.
Malicious attachments
Attackers will email attachments containing malware disguised as harmless Word documents, PDFs, images, etc. The message in the email will try to persuade you to open these attachments, allowing the attackers to steal your information or take control of your devices. The emails will often impersonate university organizations or officials to trick you into opening them.
Requests for money, gift cards, etc.
Criminals will often impersonate university leadership, requesting money, gift cards, or financial or personal information. They may also ask you to log in to a university account, such as CIS, using a provided link that allows them to steal your credentials or infect your devices.
Example: Financial scamReport a phish
If you receive a phishing attempt through a university email account, the Information Security Office (ISO) asks that you immediately report it using the Phish Alert Button.
- Open or select the suspicious message, then select the Phish Alert Button to send it to the ISO for review.
- If your email client does not have the Phish Alert Button, forward the email as an attachment to phish@utah.edu.
- For more info on how to report suspicious emails, please visit this IT Knowledge Base article.
After reviewing the suspicious email, the ISO will notify you whether it is a phishing attack. If the message is malicious, the ISO will remove it from your inbox and act as needed to protect users and the university.
If, by accident, you open a questionable link and enter login credentials, immediately go to CIS — https://cis.utah.edu/ — and change your password. In addition, contact the ISO's Security Operations Center at soc@utah.edu to notify information security staff.
If you need additional assistance, please contact your central IT help desk:
- Main Campus UIT Help Desk: 801-581-4000
- University of Utah Health ITS Service Desk: 801-587-6000
![]()
Report a scam
To make a police report regarding a scam, call the University of Utah Police at 801-585-2677 and ask to speak with an officer. This request will create a call log, which will show the date, time, and nature of your complaint. After speaking with an officer, you will receive instructions on next steps.
Social engineering
Social engineering is the practice of trying to trick or manipulate people into breaking normal security procedures. In general, the principle behind social engineering, phishing, and scams is that people are the weak link in security — it can be easier to trick people than to hack into computing systems by force.
Social engineers exploit people’s natural tendencies to trust and help others. They also take advantage of our tendency to act quickly when faced with a crisis. Phishing is a form of social engineering.
Other types of phishing
Phishing can extend beyond scams sent via email. Criminals also use phishing tactics and social engineering in text messages (smishing) and phone calls (vishing).
Vishing (voice phishing)
In voice phishing, the phisher calls someone and asks them to provide sensitive personal details or dial a number, according to KnowBe4. The purpose is to steal personal or bank account information through the phone. Vishing is mostly done with a fake caller ID.
Smishing (SMS phishing)
Smishing is phishing conducted via short message service (SMS), a telephone-based text messaging service, according to KnowBe4. A smishing text, for example, attempts to entice a victim into revealing personal information via a link that leads to a phishing website.