You’re accessing archived content
This is archived content from the UIT website. Information may be outdated, and links may no longer function. Please contact stratcomm@it.utah.edu if you have any questions about archived content.
Beware of phishing, which is becoming more popular, with these tips.
A middle-aged white man (who we will call the "fisher" from now on) wearing a green fishing vest with many pockets walks through a grove of trees, holding a fishing pole and tackle box. He has short, light brown hair and scruffy facial hair, and wears a red, white, and blue flannel shirt and jeans. He sets the pole and tackle box on the ground and stretches his arms above his head. White text flies up, reading "phish•ing." More white text follows, reading:
"phish•ing /fi-SHiNG/"
"noun"
"Tricking a user into sharing personal information or login credentials by posing as an official source."
0:09: The video transitions to the fisher sitting at a desk with two computer monitors. The monitor on the left shows a document containing a pie chart; the monitor on the right shows a yacht on water. The man rubs his hands together and cracks his knuckles, then begins to type on his keyboard. Near his keyboard, under the monitors, he has Funko Pop statues and comic book figurines.
0:13: The video transitions back to the fisher in the grove of trees. The video zooms in on the fisher's hands; he holds a small, metal box containing fishing lures. He selects a lure and attaches it to his fishing line. He then walks toward a red block U statue on the University of Utah campus.
0:23: The video moves to a shared work table, where a man and woman huddle over their Apple laptops. The white man has dark, short hair and wears a light-colored button-up shirt and khaki pants; the white woman has long, dark, wavy hair and wears a black dress. She holds a dark folder open in her lap. A woman sits adjacent to them, wearing headphones and using her Apple laptop. She has dark hair pulled into a bun and wears dark glasses and a light-colored hoodie.
0:25: The video transitions back to the fisher, who stands in front of the "Imagine U" side of Marriott Library, casting his fishing line toward the building. He walks through campus again, passing a set of stairs and multiple street lamps. He then casts his line toward a white female student passing by on the sidewalk, which is lined with trees full of leaves. The red block U is behind him on the left. The student — who is wearing a multicolored, short-sleeved shirt with chevron patterns, black pants, and a backpack — shies away.
0:35: The fisher continues casting his line in various places around campus. In one scene, he even pops out beyond a bush to startle a man passing by. The white man is wearing a blue button-down shirt with the sleeves rolled up and jeans. In another scene, the fisher casts his line toward a white male man who is walking his bike on the sidewalk. The cyclist has long light brown or blond hair, and wears red flannel, dark jeans, a red and white hat, and a backpack and carries a light-colored helmet. He ducks from the fishing line.
0:41: In the next scene, the fisher climbs a rock and looks out over the landscape. He then appears to reel in his fishing line, which is taut. Text fades in from the left, reading "You will never receive a threatening or intimidating email from any legitimate University source."
0:48: The video transitions to a man, whose face we cannot see, typing on a black laptop with a U drum and feather sticker and a white sticker in the shape of Alaska. He is wearing a white shirt with a dark graphic, Apple headphones, and a red and white braided bracelet. On the desk, there is a couple of notebooks, and red and blue pens. Light filters in behind him. Text fades in from the left, reading "Never share your uNID and password with anyone."
0:53: The video transitions to a black screen that shows icons and text on the common signs of phishing scams, including the "no" symbol and a tip that reads: "Common Phishing Scams." A pointer moves to reveal the following bullet points:
- "Unusual email language, poor spelling or grammar"
- "The URL doesn't match webpage"
1:02: The video then moves to into an example of a webpage in the Safari browser. The URL reads "www.TAKEALLYOURMONEYANDRUN.org," and the page imitates a University of Utah login screen. A browser tab in the background reads, "Funny Cats — YouTube." The video zooms in on the URL, which is highlighted with a white overlay while the rest of the screen is darkened by a black overlay.
1:05: The video returns to the bullet point list of common phishing scams. The next item reads, "When hovering over link, it doesn't match the promised content."
1:08: The screen transitions to an email client, which shows an example of an email. Highlighted is a link that reads, "here" but shows a URL to "http://takeallyourmoneyandrun.org."
1:11: The video transitions into a library, where an Asian man sits at a desk with his hands on the keyboard of the laptop open in front of him. He is wearing a checkered button-down shirt with the sleeves pushed up and a pair of glasses. His hair is black and a bit long around the ears, forehead, and back of the neck. A backpack or messenger bag is on the table next to his laptop, and a chair is open to his left. In the background, light filters in from large windows and two stacks/shelves hold numerous books.
1:15: The video zooms in on the Asian man and his laptop. On the screen, text reads "Guard your uNID and password like your Social Security number." Then video transitions into a montage of shots of people using open laptops. The first image shows a desk with an open laptop, which has multiple windows open. White hands barely touch the edge of the keyboard. Text fades in that reads "Change your password often." The second image shows a white man using the touch pad on his laptop to scroll. We only see his hands and the sleeves of his button-down shirt, which is white checkered with dark lines. The third image shows a white woman using a silver laptop. She faces us so we cannot see what is on the screen. She has long, brown hair and wears a dark T-shirt. To her right, another white person, who appears to be a woman, types on a laptop. This person is wearing a gray sweatshirt or hoodie. Text fades in that reads "Change your password and call the Campus Help Desk immediately." A phone number reading "801-581-4000" fades in.
1:25: The video transitions back to an outdoor space on campus with grass and trees. A man in a light blue-green shirt and dark pants walks left past our view. Another man, somewhat balding, walks right past our view. He wears a dark blue or black shirt with short sleeves and a collar, and jeans. The fisher is in the background, waving his fishing line.
1:29: The video returns to the fisher's desk, with a close-up on the Funko pop and comic book figurines. The figurines include Superman and a shark, but it's not clear which characters the others represent. The video zooms out so we can see the fisher sitting at the desk. He makes a fist with his right hand and pulls it downward in a motion that represents cha-ching, yes, score, gotcha, or a similar celebration. He throws his head back and laughs.
1:32: The screen goes black. The University Information Technology (UIT) logo (white text with a red Block U) and white text reading "it.utah.edu/" fade in, with the word "security" added shortly after to the end of the URL so it reads "it.utah.edu/security."
1:37: The screen changes to a white background with a gray gradient at the bottom that shows a mirror image of the red and black Imagine U logo in the center of the screen.
Phishing is becoming more and more popular.
We're talking about phishing with a "ph." Not the river-runs-through-it kind.
It's about cyber scammers, con artists, and thieves. Every day they're baiting and hooking personal information and gutting bank accounts. It's happening all around the nation and right here at the U.
Faculty, staff, and students are all vulnerable, and attacks are becoming more targeted.
Because some university personal information is readily available, scammers are often using it, along with emotional responses, to get you to act.
It's important to stay vigilant and know thieves are trying to land the big one.
You will never receive a threatening or intimidating email from any legitimate university source.
Don't take the bait. Never share your uNID and password with anyone. And look for the signs that are common in phishing scams. Things like:
- unusual email language or spelling or grammar
- the URL doesn't match the webpage
- when hovering over a link, it doesn't match the promised content
Here's what to do to stay protected:
- Guard your uNID and password like your Social Security number
- Change your passwords often
- Lock your screens when not in use or when you leave your desk
If you've been hooked, call the Campus Help Desk (801-581-4000, option 1) immediately.
Trust your gut. If it smells fishy, it probably is.
For more information, visit it.utah.edu.
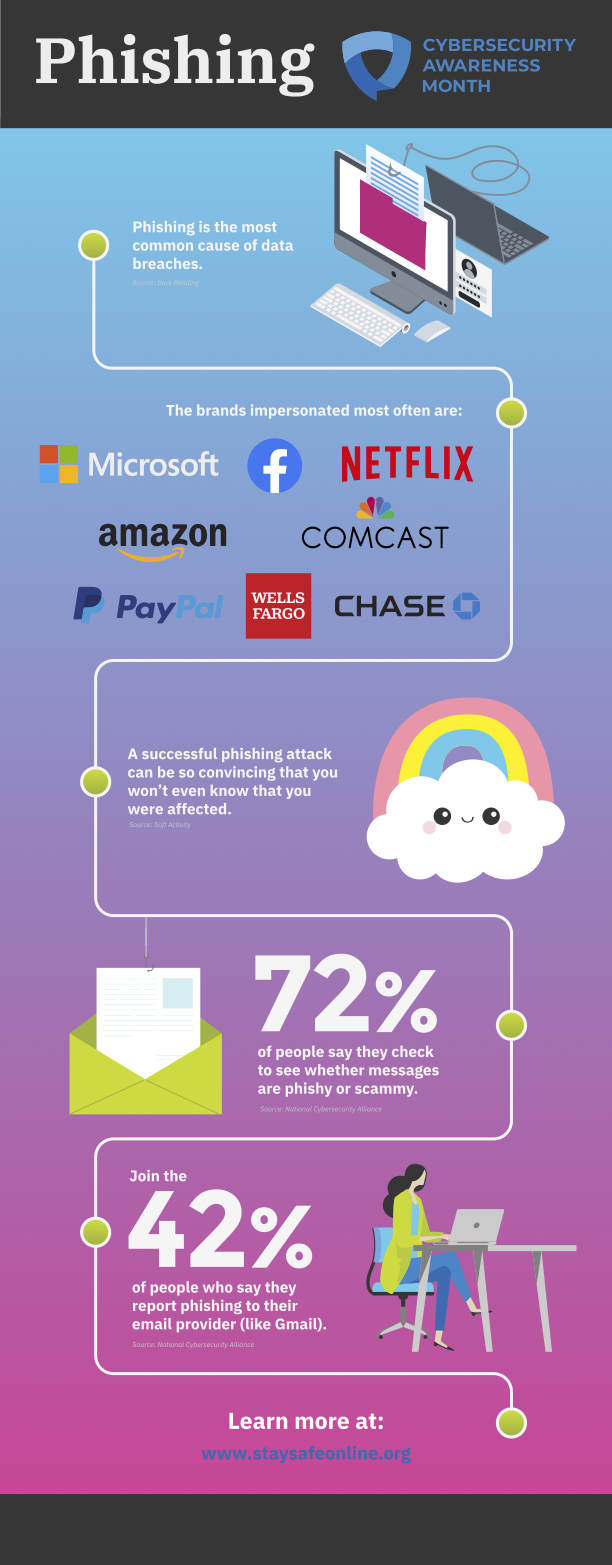
Select the image for a larger version.
An infographic on phishing, with the Cybersecurity Awareness Month logo in the top right and a blue to pink gradient for a background. A line flows from top to bottom with green dots marking important facts.
Fact 1: Text that reads, "Phishing is the most common cause of data breaches." to the left of a graphic of a desktop computer and laptop show the laptop using a line with a hook to phish a document contained in a pink folder on the desktop. The phisher wants credentials, shown to the right.
Fact 2: Text that reads, "The brands impersonated most often are:" with the Microsoft, Facebook, Netflix, Amazon, Comcast, PayPal, Wells Fargo, and Chase logos below the text.
Fact 3: Text that reads, "A successful phishing attack can be so convincing that you won't even know that you were affected." to the left of an illustration of a pink, yellow, and blue rainbow that sits on top of a white cloud with googly eyes and rosy cheeks.
Fact 4: Text that reads, "72% of people say they check to see whether messages are phishing or scammy." to the right of an illustration of a green email icon with an open document that's hanging on a fishing hook.
Fact 5: Text that reads, "Join the 42% of people who say they report phishing to their email provider (like Gmail)." to the left of an illustration of a woman sitting at a desk and using a laptop computer. The woman wears an open, green sweater, blue shirt, and blue pants. She sits on a blue office chair.
Learn more at: wwww.staysafeonline.org
How to recognize phishing
Phishing is a scam designed to steal information or passwords, compromise devices, or trick you out of money. While we often think of phishing as being limited to emails, it can also take the form of deceptive text messages (smishing), posts on social media, pop-ups, or phone calls (vishing).
Phishers may ask for your name, account information, date of birth, Social Security number, address, etc. They may also try to get you to open a link or file. Hover or tab over any links to review exactly where you are being directed. If it's not legit, don't open it.
Types of phishing and phishing “hooks”
Phishing is a way criminals use social engineering to trick you into sharing private and confidential data, such as bank account numbers or login information. Criminals employ many methods, such as:
- Phishing
- Generic, everyday phishing is not targeted and tends to be easier to spot.
- Spear phishing
- Spear phishing is one of the most dangerous forms of phishing. The phisher targets a specific individual and studies them to be able to write a more convincing, legitimate-looking message to trick them into letting down their guard and sharing sensitive information.
- Whaling
- Also known as CEO fraud, whaling specifically targets chief executive officers and senior leadership.
- Shared document phishing
- You might receive an email that appears to come from file-sharing sites like UBox, Dropbox, Google Drive, or OneDrive alerting you that a document has been shared with you. The link provided in these emails will take you to a fake login page that mimics a real login page and will steal your account credentials.
Indicators that an email isn’t legitimate:
- The sender isn’t specified, isn’t someone you know, or doesn’t match the “from” address
- Unfamiliar, unusual, or generic greetings; it’s not addressed to you, specifically,
by name
- [No greeting]
- Dear member
- Hello friend
- Spelling and grammar errors
- Suspicious links
- A link that doesn’t match the URL of the webpage stated in the email
- A link to pictures or videos from people you don’t know
- A link or attachment to view an unexpected e-card or to track an unknown package
- Attachments
- Incorrect or suspicious filenames
- Suspicious file extensions (e.g., .bin, .com, .exe, .html, .pif, .vbs, .zip, .zzx)
- Low-resolution images
Reputable organizations like the University of Utah will never email you for your password, Social Security number, or any confidential or personal information. Visit our Phish Tank to learn more about various phishing schemes and how to avoid them.
How to report phishing
If you receive a phishing email in your UMail account, immediately report it using the Phishing Alert Button — the simplest and the fastest way to report suspicious messages to the Information Security Office (ISO).
If your email client does not have the Phish Alert Button, forward the email as an attachment to phish@utah.edu. If you are unsure how to forward a message as an attachment, use a search engine (e.g., Google) to find instructions for your email client.
Once you report the email, the ISO’s Security Operations Center (SOC) will review the suspicious email, notify users whether it is malicious, and act as needed to protect users and the university.
If, by accident, you open a questionable link and enter your university credentials, immediately go to the CIS website — https://cis.utah.edu/ — and change your password. In addition, contact the SOC at soc@utah.edu to notify information security staff.
