You’re accessing archived content
This is archived content from the UIT website. Information may be outdated, and links may no longer function. Please contact stratcomm@it.utah.edu if you have any questions about archived content.
Case review: The risks of ransomware
Plus, our tips on how to prevent and respond to an attack
To illustrate the damage that ransomware can cause, let's look at a report from a 2019 information security incident in Lake City, Florida, where about 12,000 people reside.
According to “The 2021 Ransomware Survival Guide” by Proofpoint, an attacker encrypted the city’s computer system, locking out city officials. “Phones were down, email was out of commission, computers did not work and even the photocopiers were inoperable,” The New York Times reported.
It started when several city employees fell for a phishing attack, opening an email and attachment seemingly from a known contact with a subject line like “you have an invoice ready.” The New York Times said the email “was really a spear phishing attack, using what is known as Ryuk ‘triple threat’ ransomware.”
To regain access to the city’s network and decrypt all the data, the city’s insurer paid a ransom of $460,000. Afterward, it still took several weeks for officials to fully restore IT infrastructure for the city.
How ransomware works
Simply put, ransomware is a type of cyberattack that can cause serious damage to your data and devices, as well as financial loss and other, more significant consequences.
Ransomware attacks usually start with malware sent in a phishing email. The malware encrypts your local data and then starts to encrypt all the data on the devices connected to your shared networks (e.g., school, work, and home), holding that data hostage. In other words, the encryption process “kidnaps” the data by transforming it into something you don’t have access to, and to regain access you need a decryption key that only the person behind the ransomware attack has. Once the attacker encrypts your data, they ask for a ransom in exchange for the key that will make the data accessible again, thus the name “ransomware.”
As mentioned above, the most common way for an attacker to start a ransomware attack is by using a phishing email. These emails will contain links or attachments leading to the download of the malware that will encrypt the data. For that reason, be extra cautious with emails that you do not recognize, and never open a link or download an attachment without checking the source. For more tips, please visit Phishing fundamentals: 3 tips to shore up your defenses.
Attackers may also distribute malware through websites, links, social media, advertising (malvertising/pop-ups), and other entrance vectors caused by outdated software.
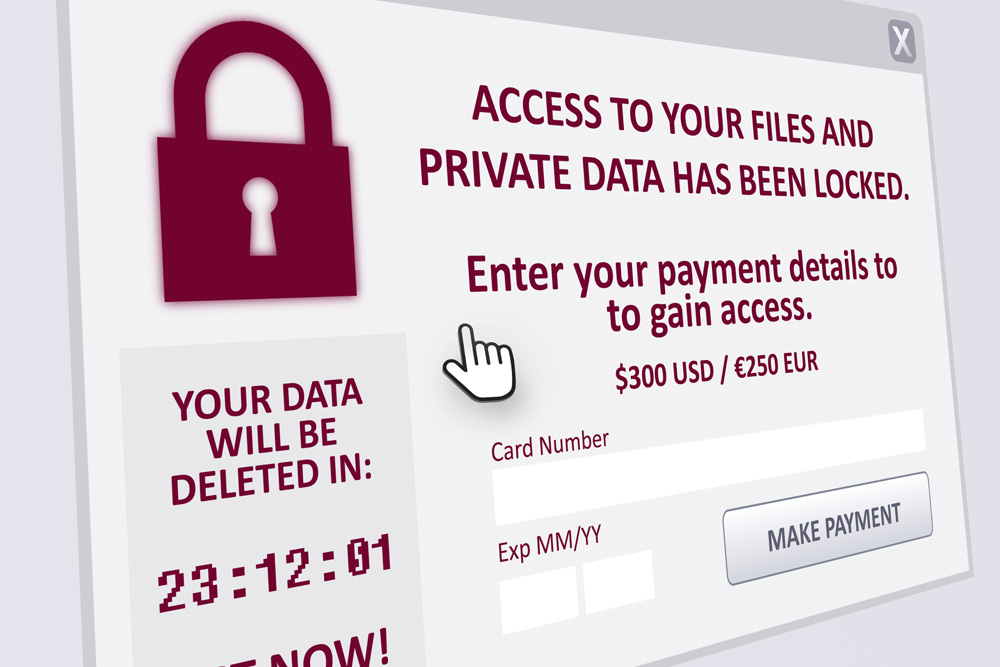
If you believe that you may have downloaded malware to a university-owned device, immediately disconnect the device from the network to avoid spreading the malware and infecting other devices.
How to respond to an attack
To reduce the risks of a ransomware attack, be sure to maintain regular system backups and practice restoring data from them to become familiar with the process. Also, you should regularly update and patch software to avoid known vulnerabilities.
If you receive a suspicious email in your UMail inbox, report it immediately by forwarding the email as an attachment to phish@utah.edu. And if you haven’t done so yet, please take the Security Awareness training course in Canvas.
If you believe that you may have downloaded malware to a university-owned device, immediately disconnect the device from the network (detach the internet cables and turn off your Wi-Fi) to avoid spreading the malware and infecting other devices. You should also contact ISO’s Security Operation Center at soc@utah.edu. Never try to solve the problem by yourself using free ransomware decryption tools, which could cause more harm than good.
You should also report the incident to U Police at uupd-tips@utah.edu. Ransomware is a form of extortion and a crime.
Resources
- Phishing Knowledge Base article
- Protect your computer or device Knowledge Base article
- Report a security incident Knowledge Base article
- CISA's Stop Ransomware website
- FBI's Common Scams and Crimes: Ransomware
- Internet Crime Complaint Center (IC3): Ransomware
If you want to dive deeper and strengthen your knowledge about ransomware, the following blogs are great resources:
- CTB-Locker: http://blog.kaspersky.com/new-version-ctb-locker/
- CryptoLocker: http://blogs.cisco.com/security/talos/cryptowall-3-0
- TeslaCrypt/AlphaCrypt: https://blog.kaspersky.com/teslacrypt-ransomware-targets-gamers/
